About this Article
This article provides information related to Closed loop ACP feature added as a part of VSP 3.1.0.
Introduction
VSP works on Positive ACP Model BUA (Block Unless Allowlisted) - Only the processes that are added to the allowlist can be executed on the Workload/Probe. All the other processes are blocked. These rules are applied to Operating System commands also. Example: bash, cmd.
Commands can be initiated by the operating system, an application (workload) or a user. When an application/workload executes a process (Example: ps) periodically, VSP generates incidents for every execution.
LOLBins
- These are the executables that are installed (by default) as part of an operating system
- They can be executed by any local service or application OR by a remote user by connecting to the workload
- Executables that are added by users for legitimate purposes could be exploited as a LOLBin. In many scenarios, if it is a part of some common third party software installation it can be exploited
LOLBins can be invoked as a
- Benign Execution - An example is when a local service or application executes a routine command to copy a log file
- Malicious Execution - If an attacker gains control of the application and uses it to execute malicious code
Closed Loop ACP Engine can differentiate between these two types of execution and block only the malicious execution while allowing the benign execution. This is explained in the next section in detail.
Workflow
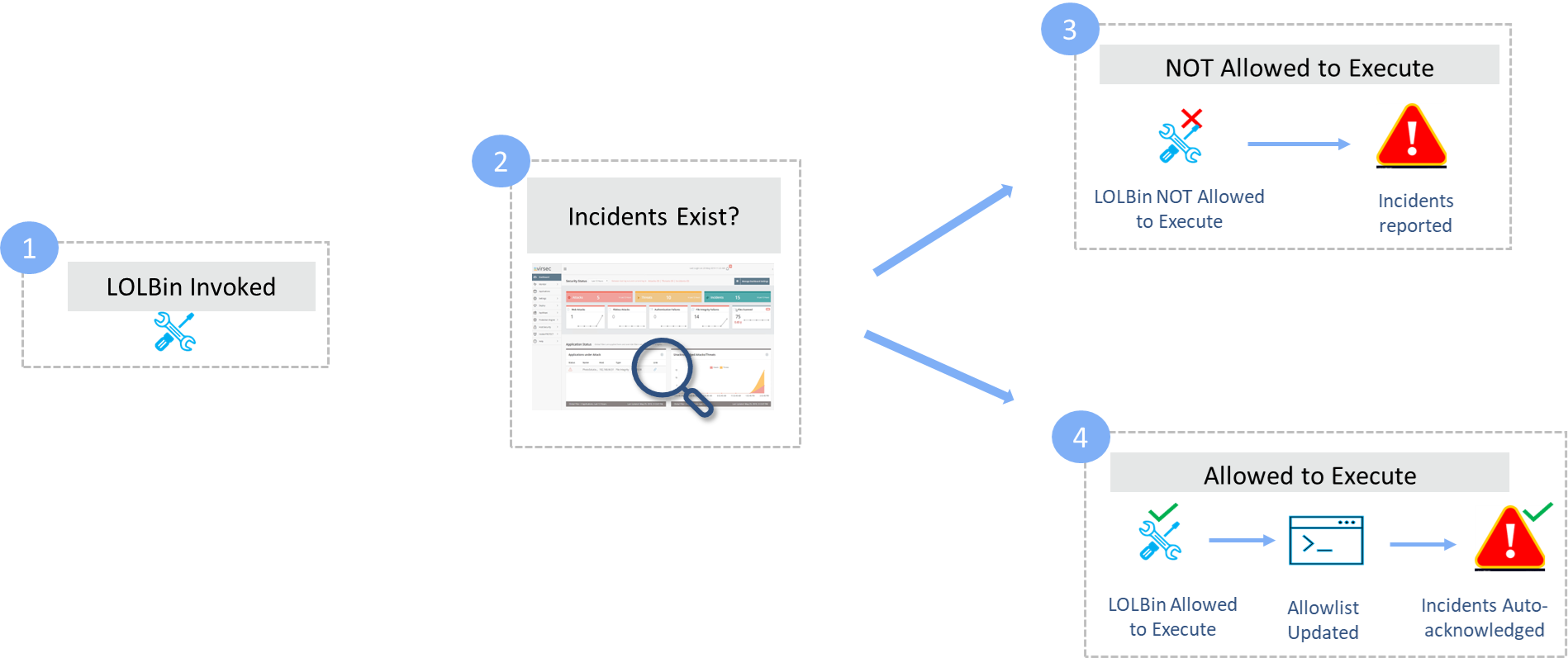
- When a LOLBin is invoked, the closed loop ACP engine checks whether incidents exist for the associated host/workload or not
- When an application is attacked/compromised, multiple VSP engines generate incidents. If such incidents exist, ACP engine determines that the LOLBin is executed with malicious intent. Such processes are NOT allowed to execute
- Alternatively, if incidents do not exist for the workload, it indicates that the application is not compromised. In such scenarios, ACP engine concludes that the LOLBin is NOT invoked with malicious intent and is allowed to execute after verification. If incidents are reported, they are auto-acknowledged by the ACP engine itself
- Admin users need to add ACP Allow rules to carry out their routine commands. Click here to view information about the APIs that can be used to add Allow rules