About this Article
This article provides all the required information related to Host Profiles (for VM) and Host Template (for containers) - Creation, Modification, Deletion and Import/Export of Profiles on CMS.
Create Host Profile (VMs only)
To create a profile, follow the below steps:
sNavigate to Manage > Host > Host Protection in the left navigation pane. Click ADD PROFILE
Provide the below information
Field Name
Description
Name
Name of the profile
Profile Tag
Tag used during VM Probe auto registration
Library Monitoring
Select the box to enable Library Monitoring
Memory Exploit Protection
Enable it for Memory Exploit Protection functionality
Auto Allowlist
Auto allowlist files with reputation ”SAFE”
Trust Threshold for Auto Allowlisting
Files of equal and above the configured Trust threshold value are auto allowlisted. Available options are Full, Elevated, High, Medium and Low
Auto Allowlist Unknown files from Discovery Scan
Auto allowlist files with reputation “UNKNOWN”
Auto Allowlist Unknown files from Discovery Scans and Incidents
Auto allowlist files with reputation “UNKNOWN” and source “INCIDENTS”
Allow New Publisher/Package
Auto allowlist any new publisher/package detected due to new software installation OR new instance association with the profile
When enabled, the publisher/package is automatically added to the allowlist with the source as “SCAN”. When Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, they are listed in the respective lists with the source as “Incident” without any incidents reported in CMS
When disabled and the Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, incidents are reported with the Publishers/Packages listed in the respective lists with the source as “Incident”
The user can modify the allowlist as required at any point. The modified list is published to the Probe
Operating System
Select the Operation System – Windows/Linux - from the drop-down list
App Control Policy Name
(Optional) Select the appropriate App Control policy from the drop-down list
Default Monitoring Mode
Select the Default Monitoring Mode for
Executable Protection: Available options are Protect, Detect or Disable
App Control Policy: Available options are Protect, Detect or Disable. Ensure that the App Control Policy Name is provided to set the default monitoring mode
Memory Exploit Protection: Available options are Protect, Detect or Disable. Ensure that the Memory Exploit Protection field is enabled to set the default monitoring mode
Click here for more information about the allowed configurations for Executable Protection and ACP modes
Protection Profile Name
(Optional) Select the appropriate Protection profile from the drop-down list. Based on the selected Host OS, Protection Profiles relevant to that OS are populated
Exclusions for Allowlist
This is the list of directories that need to be excluded from host monitoring. Executables launched from these directories are not reported as incidents. Add the directories individually and press return key. Normal regex syntax can be utilized. This is a local list applicable only to the profile being created. By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.
Exclusions for Memory Exploit Protection
This is the list of directories that need to be excluded from Memory Exploit Protection. By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.
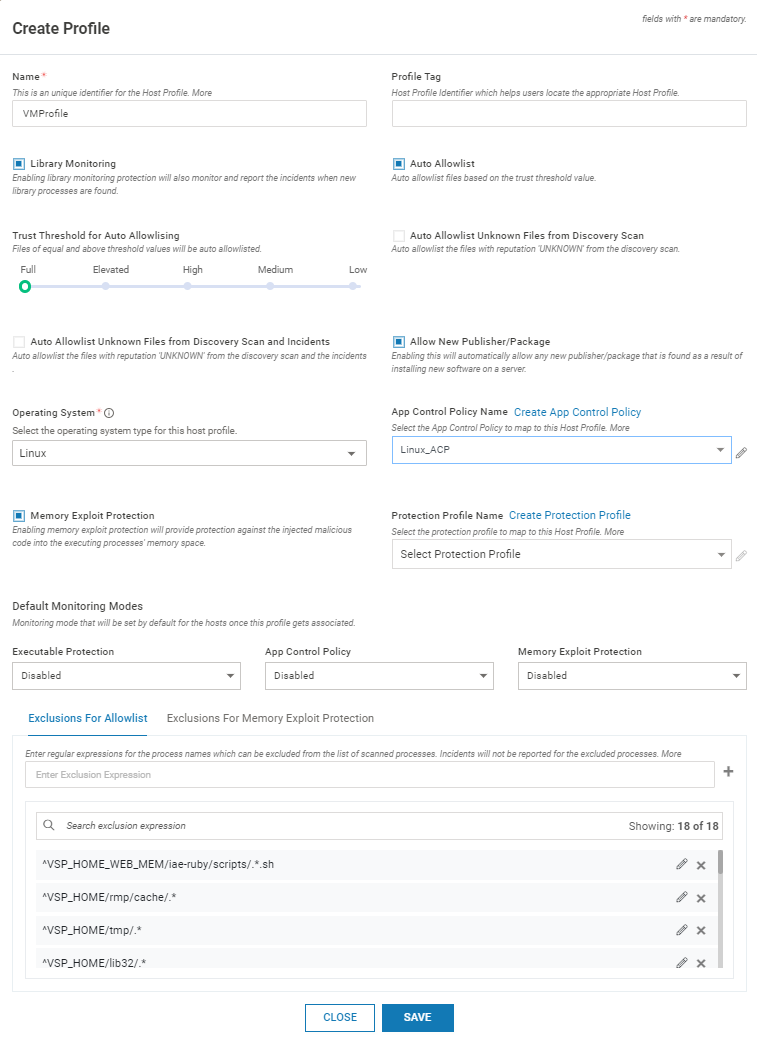
Click SAVE
The created profile is listed on the Host Monitoring page
Navigate to Manage > Host > Host Protection in the left navigation pane. Click ADD PROFILE
Provide the below information
Field Name
Description
Name
Name of the profile
Profile Tag
Tag used during VM Probe auto registration
Library Monitoring
Select the box to enable Library Monitoring
Memory Exploit Protection
Enable it for Memory Exploit Protection functionality
Auto Allowlist
Auto allowlist files with reputation ”SAFE”
Auto Allowlist Unknown files from Discovery Scan
Auto allowlist files with reputation “UNKNOWN”
Auto Allowlist Unknown files from Discovery Scans and Incidents
Auto allowlist files with reputation “UNKNOWN” and source “INCIDENTS”
Allow New Publisher/Package
Auto allowlist any new publisher/package detected due to new software installation OR new instance association with the profile
When enabled, the publisher/package is automatically added to the allowlist with the source as “SCAN”. When Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, they are listed in the respective lists with the source as “Incident” without any incidents reported in CMS
When disabled and the Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, incidents are reported with the Publishers/Packages listed in the respective lists with the source as “Incident”
The user can modify the allowlist as required at any point. The modified list is published to the Probe
Operating System
Select the Operation System – Windows/Linux - from the drop-down list
Default Monitoring Mode
Select the monitoring mode as Protect or Detect
App Control Policy Name
(Optional) Select the appropriate App Control policy from the drop-down list
Protection Profile Name
(Optional) Select the appropriate Protection profile from the drop-down list. Based on the selected Host OS, Protection Profiles relevant to that OS are populated
Exclusions for Allowlist
This is the list of directories that need to be excluded from host monitoring. Executables launched from these directories are not reported as incidents. Add the directories individually and press return key. Normal regex syntax can be utilized. This is a local list applicable only to the profile being created. By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.
Exclusions for Memory Exploit Protection
This is the list of directories that need to be excluded from Memory Exploit Protection. By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.
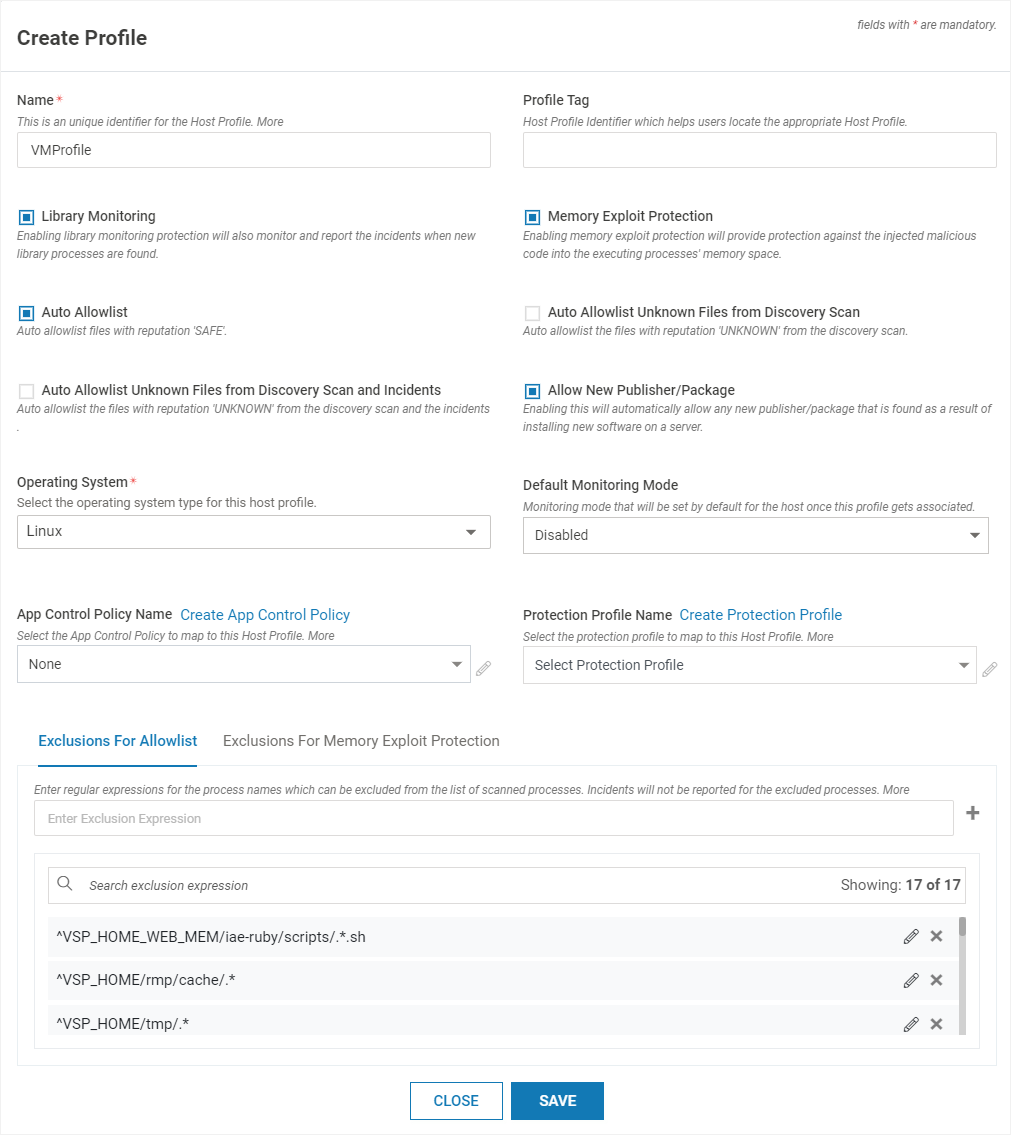
Click SAVE
The created profile is listed on the Host Monitoring page
Navigate to Manage > Host > Host Protection in the left navigation pane. Click ADD PROFILE
Provide the below information
Field Name
Description
Name
Name of the profile
Profile Tag
Tag used during VM Probe auto registration
Library Monitoring
Select the box to enable Library Monitoring
Memory Exploit Protection
Enable it for Memory Exploit Protection functionality
Auto Allowlist
Auto allowlist files with reputation ”SAFE”
Auto Allowlist Unknown files from Reference Host Scan
Auto allowlist files with reputation “UNKNOWN”
Auto Allowlist Unknown files from Reference Host Scans and Incidents
Auto allowlist files with reputation “UNKNOWN” and source “INCIDENTS”
Allow New Publisher/Package
Auto allowlist any new publisher/package detected due to new software installation OR new instance association with the profile
When enabled, the publisher/package is automatically added to the allowlist with the source as “SCAN”. When Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, they are listed in the respective lists with the source as “Incident” without any incidents reported in CMS
When disabled and the Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, incidents are reported with the Publishers/Packages listed in the respective lists with the source as “Incident”
The user can modify the allowlist as required at any point. The modified list is published to the Probe
Host Name
Select the name of the host from the drop-down list
Default Monitoring Mode
Select the monitoring mode as Protect or Detect. This is applicable for all hosts except the reference host used to create the allowlist. Ensure that the monitoring mode is explicitly set for the reference host once the host scan is complete and the allowlist is published. For subsequent hosts associated with the profile, the default Mode is applied automatically
App Control Policy Name
(Optional) Select the appropriate App Control policy from the drop-down list
Protection Profile Name
(Optional) Select the appropriate Protection profile from the drop-down list. Based on the selected Host OS, Protection Profiles relevant to that OS are populated
Exclusions for Allowlist
This is the list of directories that need to be excluded from host monitoring. Executables launched from these directories are not reported as incidents. Add the directories individually and press return key. Normal regex syntax can be utilized. This is a local list applicable only to the profile being created.
Version 2.9 : By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.Exclusions for Memory Exploit Protection
This is the list of directories that need to be excluded from Memory Exploit Protection.
Version 2.9 : By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.Click SAVE
The created profile is listed on the Host Monitoring page
In both Windows and Linux, the mounted folders are auto-excluded during the initial system scan
The below icon is displayed when the scan is in progress. Expand the profile to view more information
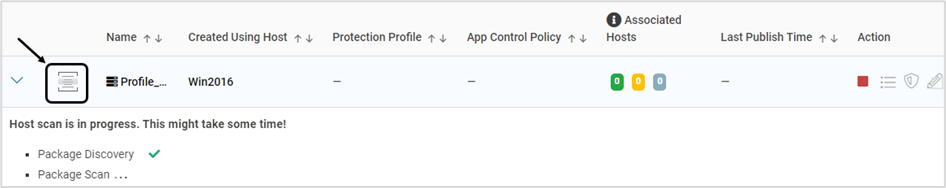
Once the scan is complete, click the icon below
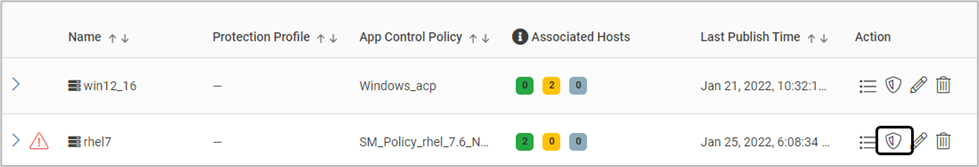
The warning message below is displayed
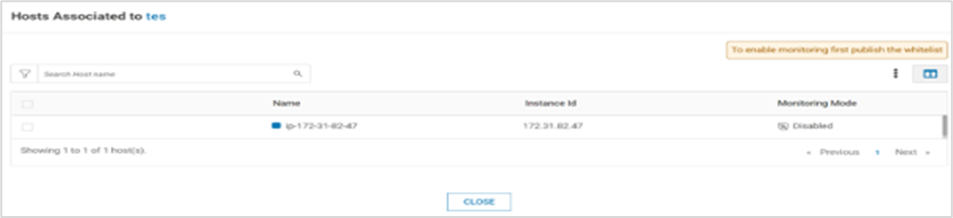
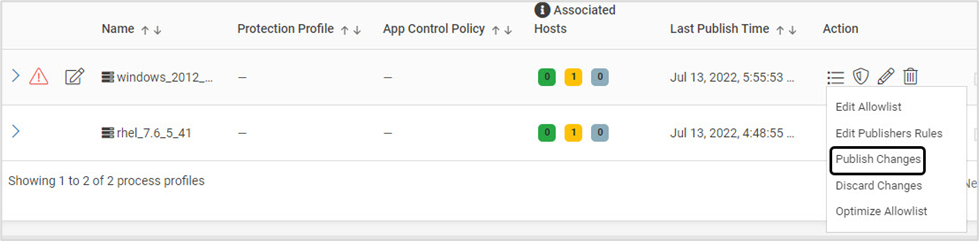
Click Edit AllowList and allow the execution of required files, libraries and scripts
Click Publish Changes to update the associated host
Host Profile Workflow (Containers)
Follow the below workflow to generate Host Profile:
Create a pod template host profile with the required settings. The created template is used for all new VSP-protected pods/containers that come up
Run the application container through VSP CI and CD tools to enable VSP protection for a given application container
Launch the VSP-protected pod/container
When the VSP controller is launched, it first registers with VSP CMS automatically by sending information about the VSP-protected application containers
A host profile is generated automatically using the pod template as a reference
Applications that share the same pod name (in K8s) OR replicas of the same container are automatically assigned to the same host profile
When the VSP Host Monitoring Module (HMM) is started, it automatically downloads the application container's allowlist generated during the VSP CI phase
VSP HMM uses the application container's allowlist and the host profile settings to determine any unknown executables
Create Host Template (Containers Only)
To create a Host template, follow the below steps:
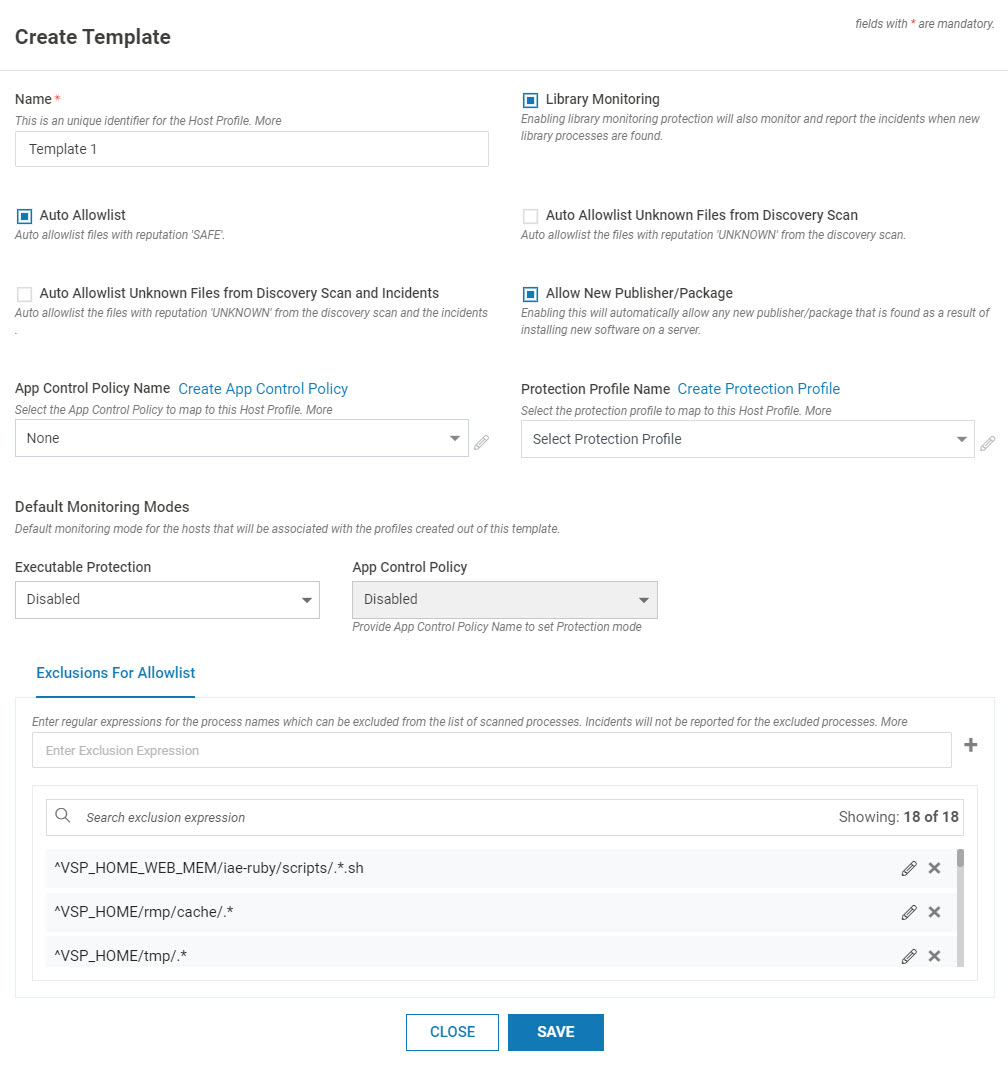
Navigate to Manage > Host > Host Protection in the left navigation pane. Click TEMPLATE
Provide the below information
Field Name
Description
Name
Name of the profile
Library Monitoring
Select the box to enable Library Monitoring
Auto Allowlist Unknown files from Reference Host Scan
Auto allowlist files with reputation “UNKNOWN”
Auto Allowlist Unknown files from Reference Host Scans and Incidents
Auto allowlist files with reputation “UNKNOWN” and source “INCIDENTS”
Allow New Publisher/Package
Auto allowlist any new publisher/package detected due to new software installation OR new instance association with the profile
When enabled, the publisher/package is automatically added to the allowlist with the source as “SCAN”. When Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, they are listed in the respective lists with the source as “Incident” without any incidents reported in CMS
When disabled and the Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, incidents are reported with the Publishers/Packages listed in the respective lists with the source as “Incident”
The user can modify the allowlist as required at any point. The modified list is published to the Probe
App Control Policy Name
(Optional) Select the appropriate App Control policy from the drop-down list
Default Monitoring Mode
Select the Default Monitoring Mode for
Executable Protection: Available options are Protect, Detect or Disable
App Control Policy: Available options are Protect, Detect or Disable. Ensure that the App Control Policy Name is provided to set the default monitoring mode
Click here for more information about the allowed configurations for Executable Protection and ACP modes.
This is applicable for all hosts except the reference host used to create the allowlist. Ensure that the monitoring mode is explicitly set for the reference host once the host scan is complete and the allowlist is published. For subsequent hosts associated with the profile, the default Mode is applied automaticallyProtection Profile Name
(Optional) Select the appropriate Protection profile from the drop-down list. Based on the selected Host OS, Protection Profiles relevant to that OS are populated
Exclusions for Allowlist
This is the list of directories that need to be excluded from host monitoring. Executables launched from these directories are not reported as incidents. Add the directories individually and press return key. Normal regex syntax can be utilized. This is a local list applicable only to the profile being created.
By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.Click SAVE
The mounted folders are auto-excluded during the initial system scan
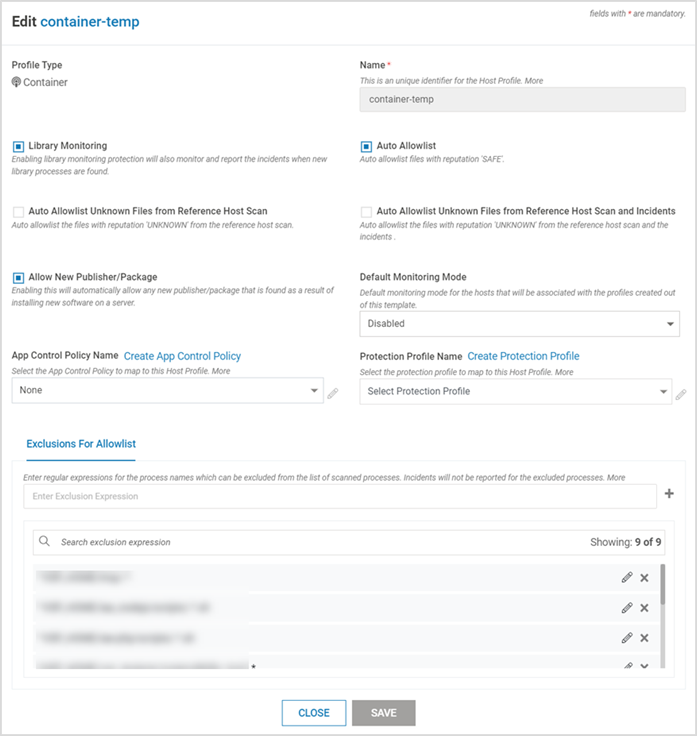
Navigate to Manage > Host > Host Protection in the left navigation pane. Click TEMPLATE
Provide the below information
Field Name
Description
Name
Name of the profile
Library Monitoring
Select the box to enable Library Monitoring
Auto Allowlist Unknown files from Reference Host Scan
Auto allowlist files with reputation “UNKNOWN”
Auto Allowlist Unknown files from Reference Host Scans and Incidents
Auto allowlist files with reputation “UNKNOWN” and source “INCIDENTS”
Allow New Publisher/Package
Auto allowlist any new publisher/package detected due to new software installation OR new instance association with the profile
When enabled, the publisher/package is automatically added to the allowlist with the source as “SCAN”. When Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, they are listed in the respective lists with the source as “Incident” without any incidents reported in CMS
When disabled and the Maintenance Mode is stopped, the newly added Publishers/Packages are listed in the respective lists. If Maintenance Mode is cancelled, only when the Publishers/Packages are accessed, incidents are reported with the Publishers/Packages listed in the respective lists with the source as “Incident”
The user can modify the allowlist as required at any point. The modified list is published to the Probe
Default Monitoring Mode
Select the monitoring mode as Protect or Detect. This is applicable for all hosts except the reference host used to create the allowlist. Ensure that the monitoring mode is explicitly set for the reference host once the host scan is complete and the allowlist is published. For subsequent hosts associated with the profile, the default Mode is applied automatically
App Control Policy Name
(Optional) Select the appropriate App Control policy from the drop-down list
Protection Profile Name
(Optional) Select the appropriate Protection profile from the drop-down list. Based on the selected Host OS, Protection Profiles relevant to that OS are populated
Exclusions for Allowlist
This is the list of directories that need to be excluded from host monitoring. Executables launched from these directories are not reported as incidents. Add the directories individually and press return key. Normal regex syntax can be utilized. This is a local list applicable only to the profile being created.
Version 2.9 and Above: By default, some directories are added to the list. Do not alter them as that can affect normal VSP functioning.Click SAVE
The mounted folders are auto-excluded during the initial system scan
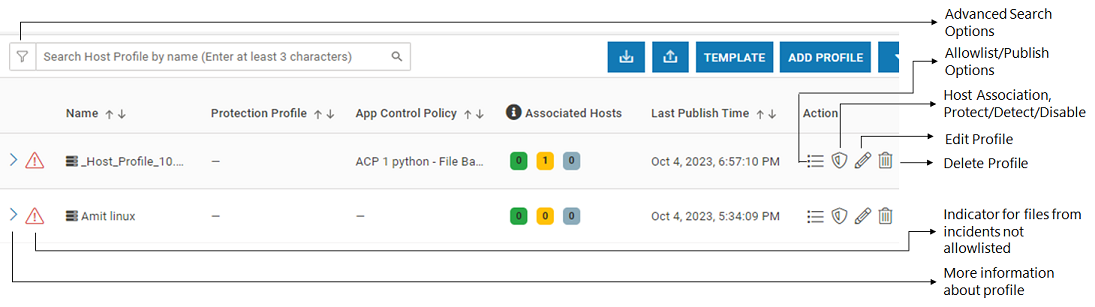
Host Profile List on CMS
Navigate to Manage > Host > Host Protection in the left navigation pane to view the Profile list
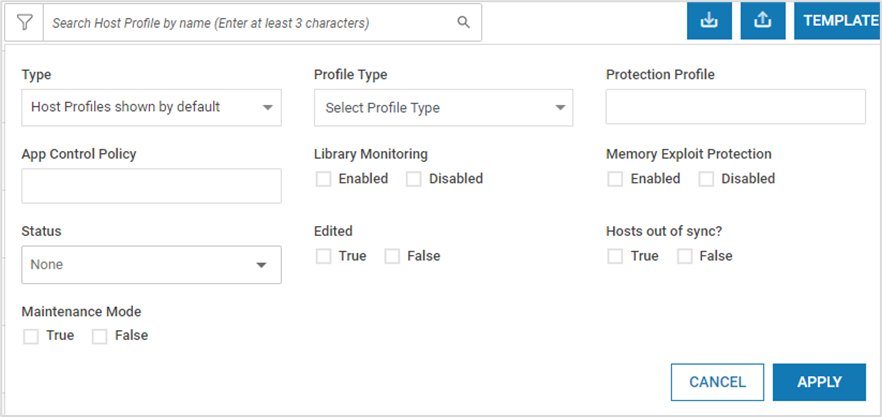
To filter the listed profiles, expand the Search option and provide the required information
Search results display the executables matching the provided criteria across profiles. This feature aids the addition or removal of a specific executable from the allowlist that is included in many profiles
Export/Import Host Profiles
Profiles can be imported or exported with .zip extension
This feature can be used during the scenario below:
When VSP protection is extended to a different environment (Example: Pre-production to Production environment)
To clone an existing entry
Ensure that import/export operations are carried out in the same VSP version. Import/export feature is compatible across various patches in the same major release (Example: VSP 2.8.x)
Export/Import of Host Profiles does not include Protection Profiles or the associated incidents
Version 2.11 and Above: Export/Import of Host Profiles includes Package/Publisher information also
Modify Profile/ Profile Template
To modify a host profile (for VM), On the Host Monitoring page, click Edit. Modify as required and click SAVE
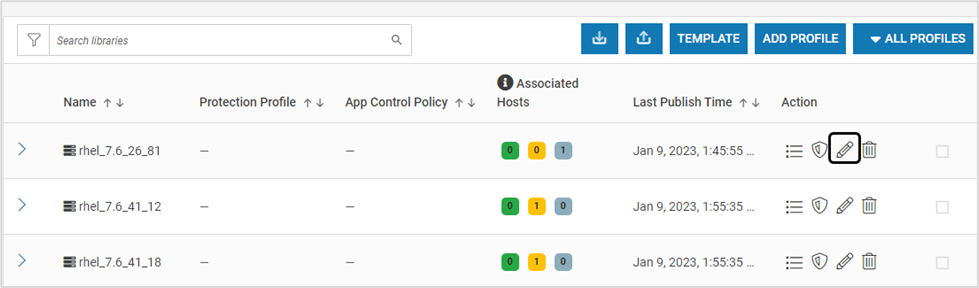
To modify the host template (for containers), On the Host Monitoring page, click TEMPLATE. Modify as required and click SAVE
Delete Profile
For containers/pods, Host Profiles are managed automatically by VSP. In case a Profile associated with a container/pod needs to be deleted, ensure that the Host Profile Template is deleted first
On the Host Monitoring page, click Delete associated with the required Profile. Click YES on the confirmation screen
Once the profile is deleted, a notification is generated