Monitor Web Protection
- 28 Oct 2024
- 4 Minutes to read
- Print
- DarkLight
- PDF
Monitor Web Protection
- Updated on 28 Oct 2024
- 4 Minutes to read
- Print
- DarkLight
- PDF
Article summary
Did you find this summary helpful?
Thank you for your feedback!
About this Article
This article provides various options to monitor and track any detected attacks/threats by VSP Web Protection.
There are three ways to monitor Web Protection by VSP:
- The widgets on the Dashboard provide a high-level view of the health of the associated hosts
- Detected attacks/threats are reported as incidents in CMS
- Reports can be scheduled as and when required for any desired time frequency
Dashboard
- Many widgets provide real-time snapshots from the configured Probes
- The dashboard contains the below tiles:
- Web Attacks - Depicts the number of Web Attacks
- Fileless Attacks - Depicts the number of Fileless Attacks
Incidents
- All the detected attacks/threats are reported to CMS as incidents. They are reported in the page
- Version 3.1.1 and Above: TrustGuardian > Incidents
- Version 3.1.0 and Below: Monitor > Incidents
- Below are the Web Attack Incident types and their description
| Event Type | Description |
|---|---|
| Command Injection | These incidents are reported when attackers attempt to smuggle malicious OS commands (arbitrary code) in the requests and execute them on the web application servers to gain control of the servers |
| CRLF Injection | These incidents are reported when attackers inject CR (carriage return) and LF (linefeed) characters into the server responses in order to carry out various attacks like HTTP response splitting, cache poisoning, information disclosure, etc |
| CSRF | CSRF (Cross Site Request Forgery) attacks are reported when an attacker, by means of social engineering or other methods, tricks victims into sending malicious web requests (e.g. transfer funds or change email addresses) without the user’s knowledge or interaction |
| Custom Attack | An injection or attack that does not fall under any existing vulnerability and can potentially be detected by configuring custom rules (deny or ratelimit). Custom injection typically works along with custom deny or ratelimit rules. |
| Custom Injection | An injection or attack that does not fall under any existing vulnerability and can potentially be detected by configuring custom rules (deny or ratelimit). Custom injection typically works along with custom deny or ratelimit rules. |
| DOM XSS | These incidents are reported when an attacker injects malicious scripts into the browser context, by manipulating DOM objects such as URL via social engineering or other methods |
| Local File Inclusion | These incidents are reported when an attacker attempts to include unauthorized server files outside the web root folder into the web process, in order to execute, upload or disclose contents of unauthorized files |
| Path Traversal | (also known as Directory Traversal) These incidents are reported when the attacker attempts to access sensitive files and directories outside the web root folder, which could lead to arbitrary code execution or sensitive information disclosure |
| Protocol Enforcement | Any protocol violation or validation failure as per the configured HTTP profile parameters (defined in web profile) are classified and reported as protocol enforcement injection. For e.g. if the user input length or number of user input goes beyond the configured value in HTTP profile, it is reported as a protocol enforcement attack |
| Reflected Cross-Site Scripting | Reflected Cross Site Scripting (Reflected XSS) attacks are reported when an attacker, by means of social engineering or other methods, tricks a victim to send malicious client-side script in web requests that is then returned by the application and executed by the victim’s browser, compromising it |
| Remote File Inclusion | Remote File Inclusion (RFI) attacks are reported where an attacker attempts to include unauthorized remote files into the web process to execute remote code or steal sensitive information |
| SQL Injection | These incidents are reported when attackers attempt to inject malicious SQL code in the requests that control SQL queries generated by the web application, in order to compromise the database integrity and contents |
| Stored Cross-Site Scripting | Stored Cross Site Scripting (Stored XSS) attacks are reported when an attacker injects malicious client-side scripts that get stored as part of the web application code, allowing attackers to compromise subsequent visitors |
| XML Injection | Reports application injection attacks embedded into XML payloads in the HTTP requests |
Exceptions Addition
[Version 3.0.0 and Above]
In cases where false positive incidents are received, VSP provides an option to add such scenarios as Exception to the associated Web Profile.
- In the left navigation pane, navigate to
- Version 3.1.1 and Above: TrustGuardian > Incidents
- Version 3.1.0 and Below: Monitor > Incidents
- Click on the required incident to view more information
- Click Add Exception to add it to the associated Web Profile
- On the pop-up window, modify the conditions as required in one of the tabs - UI Editor or JSON. The conditions are populated with the values from the reported incident. Click Save
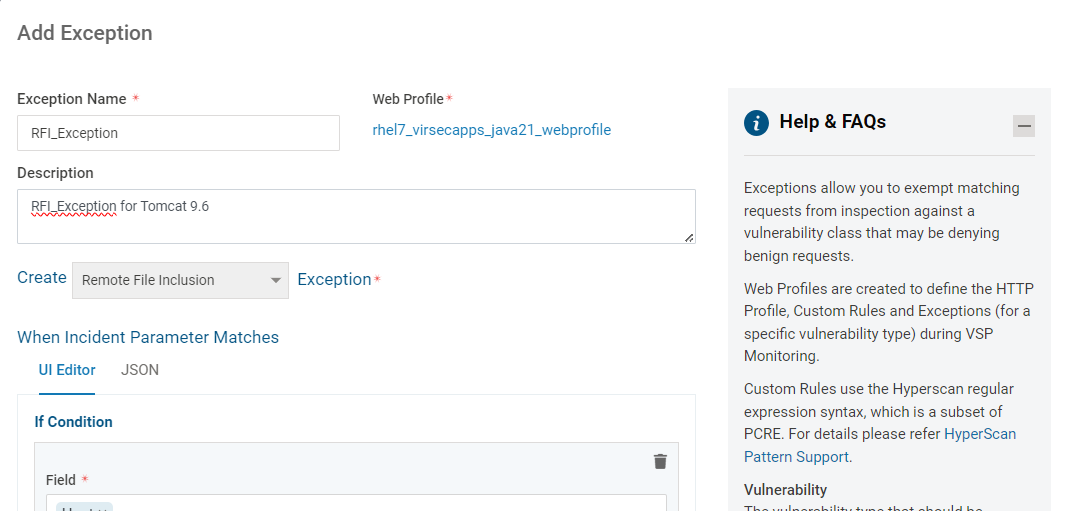
- Once the Exception is added, such incidents are no longer reported
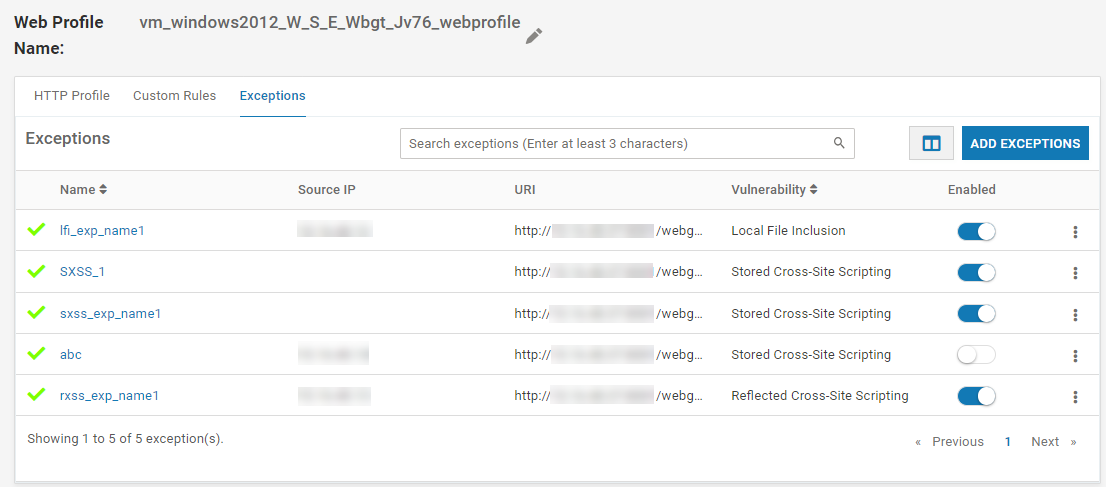
- To view the added exceptions, navigate to Manage > Web > Web Profiles in the left navigation pane. Click on the required Web Profile and navigate to the tab Exception. All the associated exceptions are listed
Reports
There are two reports that can be configured for Web Protection:
- Summary Statistics Report – Provides information related to all attacks and/or threats distributed across various vulnerabilities and hosts (where they are detected). It does NOT provide information related to Host Monitoring attacks. The first page of a sample report is provided below. The other pages provide more information for each affected application.
- Web Attacks Report – Provides detailed information related to all the web attacks detected for the configured applications across various vulnerabilities and hosts (where they are detected)
Was this article helpful?
