About this Article
This article outlines the various protection capabilities of VSP:
Host Protection - Policies for Executable Allowlisting and Application Control
Memory Protection - Safeguards against Memory Exploits and Buffer Overflows
Web Protection - Monitors user inputs, their execution, and application responses
Virsec System Integrity ensures both the provenance and integrity of authorized files, scripts, and libraries associated with the software bill of materials (SBOM). This approach enables zero trust execution and enhances existing security measures for proactive server workload protection, ensuring that these workloads remain uncompromised. The key features of the VSP Probe include: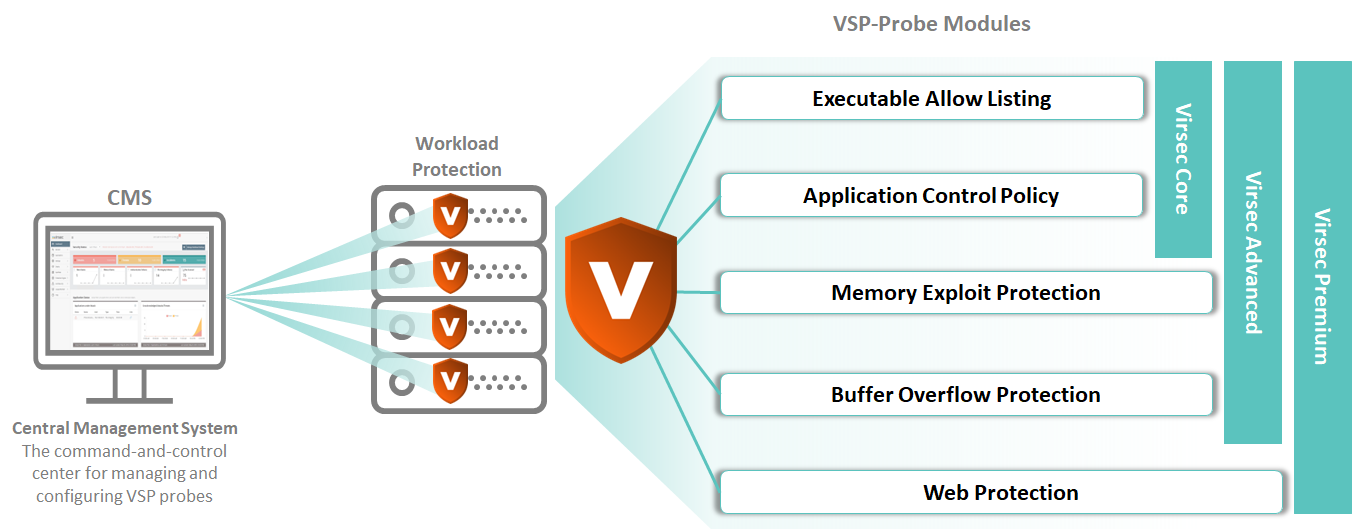
Executable Allowlisting
Virsec’s Executable Allowlisting specifies all processes and associated libraries that are permitted to execute.
Trust is established by verifying the integrity based on trusted publishers and reputation from both our database and reputable third-party sources.
System-wide allow-listing is established and enforced for processes, libraries, and scripts based on their trustworthiness.
Deviations during runtime are monitored, and any instances of executables that have been added or altered are mitigated.
Application Control Policy
The Executable Allowlisting feature of VSP guarantees that only trusted and safe processes and libraries can run on server workloads. Application Control Policies (ACP) prevent malicious actors from using advanced evasion techniques to compromise workloads.
Common use cases for Application Control Policies include:
Prevention of script-based attacks
Prevention of living-off-the-land attacks
Protection against evasion techniques
Critical data collection
Prevention of lateral movement
Protection against persistence
Prevention of remote code execution
Application Control Policies enable users to:
Implement dynamic execution control on allow-listed processes to thwart living-off-the-land attacks.
Block malicious activities from otherwise trusted operating system processes.
Enforce parent-child process controls to prevent remote code execution and lateral movement.
Add extra runtime controls to allow or disallow binary applications from spawning child processes within the scope of the binary application.
Implement additional access controls on binaries through allow or deny lists for processes, allowing specific users to run defined applications or denying them from running certain applications.
During the execution of a defined set of binaries:
Enforce specific command-line arguments and flags that are permitted.
Deny certain risky command-line arguments and flags.
Prevent binary applications from executing under all circumstances, even if they are generally trusted.
Runtime Monitoring and Protection
Virsec Runtime Monitoring and Protection enforces the provenance and integrity of the Virsec Map and the software bill of materials (SBOM) for authorized files, scripts, and libraries, ensuring they cannot be compromised and function as intended without unauthorized manipulation, whether intentional or accidental.
Memory Exploit Protection
Virsec Memory Exploit Protection prevents attempts to inject and execute malicious code from memory by targeting trusted processes.
Prevents process injection techniques, including but not limited to Code Injection, Process Hollowing, and Process Doppelgänging.
Stops the dumping of OS credentials from the memory of critical processes like LSASS (Local Security Authority Subsystem Service).
Prevents privilege escalation attacks and in-memory attacks.
Detects and halts exploit techniques in real-time without requiring signatures, learning, or customization.
Memory Exploit Protection safeguards against the following exploits or vulnerabilities:
For Windows:
Reflective DLL (Dynamic Link Library) Injection (Reported as Process Injection Incident)
Process Hollowing
PE (Portable Executable) Injection (Reported as Process Injection Incident)
Process Doppelgänging
PowerShell Exploit (Reported as Process Injection Incident)
Atom Bombing
Thread Local Storage (Reported as Process Hollowing Incident)
Thread Execution Hijack
Credential API (Application Programming Interface) Hooking
OS Credentials Dumping on Windows using LSASS
EWI - Extra Window Injection
For Linux:
DirtyCoW (Copy on Write)
tmp-fs exploit
DirtyPipe
ptrace Sudo Token Privilege Escalation
Buffer Overflow Protection
Virsec Buffer Overflow Protection maintains application control flow integrity by distinctly identifying trusted execution flow, control data, and user data from malicious events during runtime, without relying on access to source code.
Detects memory-based attacks such as buffer overflows, return-oriented programming, and other blind attack strategies targeting program flow, memory stack, and return addresses.
Protects the runtime execution of pre-compiled applications by automatically extracting the control flow for each executable and enforcing any deviations during runtime.
Web Protection
Virsec Web Protection monitors user inputs, their execution, and application responses through complex HTTP filtering, interpreter syntax mapping, and strict runtime controls to detect and prevent attacker-provided inputs to web applications.
Web Application & API Protection against attacks via the http/https channels.
Detects OWASP Top 10 Attacks on protected web applications using deep instrumentation of application frameworks and/or web servers.
Blocks web-based attacks by analyzing HTTP payloads and resulting transactions.