About this Article
This article provides an introduction to Memory Protection, protection capabilities and its workflow.
VSP Memory protection detects memory-based attacks such as buffer overflows, return-oriented programming and other blind attack schemes on program flow, memory stack, and return addresses. It protects runtime execution of pre-compiled applications by automatically extracting the control flow for every executable and enforces any deviation during runtime.
Memory Exploit Protection (MEP) is also another feature of Memory Protection stops attempts to inject and run malicious code from memory.
Buffer Overflow Protection
Virsec Buffer Overflow Protection ensures application control flow integrity by uniquely distinguishing trusted execution flow, control data and user data from malicious events during runtime without dependencies on access to source code.
- Detect memory-based attacks such as buffer overflows, return-oriented programming and other blind attack schemes on program flow, memory stack and return addresses
- Protects runtime execution of pre-compiled applications by automatically extracting the control flow for every executable and enforce any deviation during runtime
Memory Exploit Protection
Virsec Memory Exploit Protection stops attempts to inject and run malicious code from memory by targeting trusted processes
- Stops process injection techniques including, but not limited to Code Injection, Process Hollowing and Process Doppelgänging
- Stop dumping OS credentials from the memory of key processes like LSASS (Local Security Authority Subsystem Service)
- Stops privilege escalation attacks and in-memory attacks
- Exploit techniques are detected and stopped in real time without the need for any signature, learning or customization
Memory Exploit Protection provides protection against the below exploits or vulnerabilities:
For Windows:
- Reflective DLL (Dynamic Link Library) Injection (Reported as Process Injection Incident)
- Process Hollowing
- PE (Portable Executable) Injection (Reported as Process Injection Incident)
- Process Doppelgänging
- PowerShell Exploit (Reported as Process Injection Incident)
- Atom Bombing
- Thread Local Storage (Reported as Process Hollowing Incident)
- Thread Execution Hijack
- Credential API (Application Programming Interface) Hooking
- OS Credentials Dumping on Windows using LSASS
- EWI - Extra Window Injection (Version 2.10 and Above)
For Linux:
- DirtyCoW (Copy on Write)
- tmp-fs exploit
- DirtyPipe
- ptrace Sudo Token Privilege Escalation
Workflow
The workflow at a high level is provided below:
- CMS Application configuration for Buffer Error- This is covered as part of the Installation process:
- VMs - CMS applications are auto-discovered and the Probes associated with them. The security configuration must be performed for the Application processes
- Containers - CMS application must be created and configured as described here
- Ensure that the Process Type is Binary and Buffer Error is selected during Application configuration
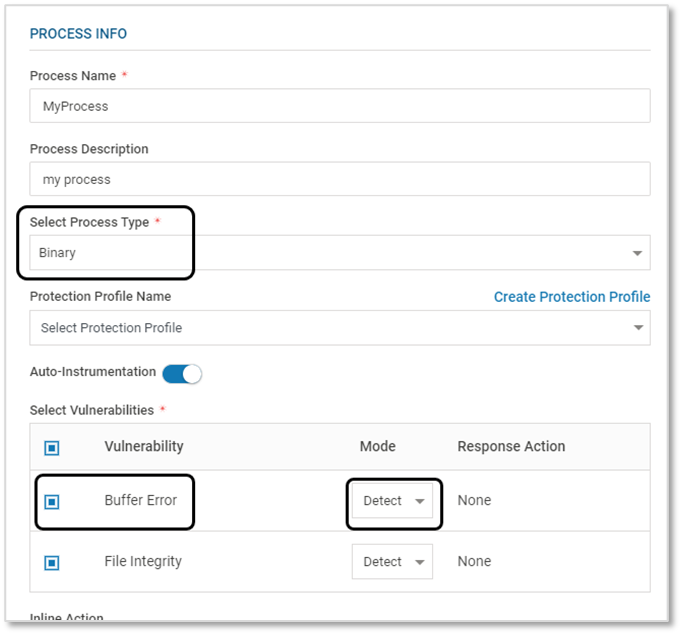
- Secure the Probe in CMS
- To enable Memory Exploit Protection, ensure that the checkbox is enabled in the associated Host Profile
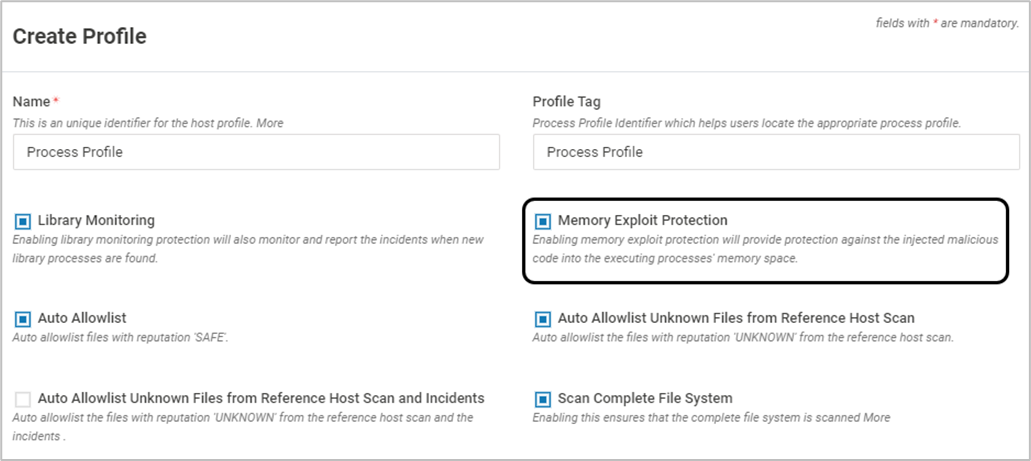
- Monitor the incidents