Threat Intelligence - An Introduction
VSP Host Protection allows users to enforce a zero-trust environment and to ensure that only the authorized and trusted executables are executed on the configured server workloads (VM or containerized). The fundamental aspect of this section is process and library control and enforcement based on the trustworthiness of those executables.
Some of the executables found on server workloads can be easily verified at the operating system level via checks like SFC validation, publisher certificates and package manager database. There is still a wide range of software that may need further review by VSP platform users. In addition, before deploying VSP security, users may want to validate that their systems are not already compromised.
To facilitate the above scenarios and use cases, Virsec Threat Intelligence Service adds file reputation capabilities to identify the known good as well as the known bad files. This is performed both during the onboard and at runtime, making operations much smoother. This can also be achieved via integration with the file reputation service of “VirusTotal”. An existing VT subscription can be leveraged. The reputation database that Virsec refers in the backend is far superior owing to VSP’s experience, especially in identifying the known good files.
Configure Threat Intelligence
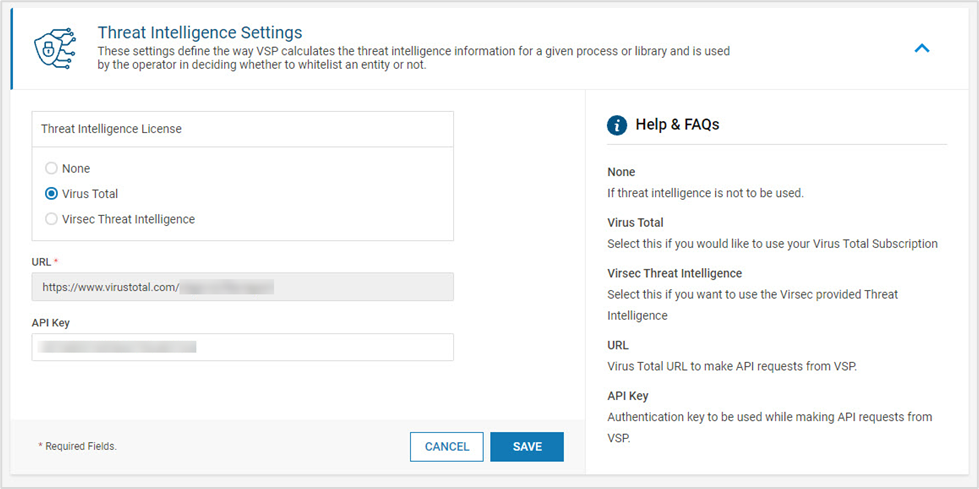
A super admin can add information related to Threat Intelligence as below
- Navigate to Administration > Configurations in the left navigation pane
- Expand Threat Intelligence Settings
- If Virus Total is already in use, it can be leveraged for VSP. Alternatively, VSP can provide integration with its Threat Intelligence Tool
- Modify as required. Click SAVE
How does it work?
Since the threat intelligence database must remain updated at all times, it is a SaaS-based service. As a result, the CMS requires constant internet access to the URLs below:
- ticloud-cdn-api.reversinglabs.com
- https://ticloud-aws1-api.reversinglabs.com
The access can be provided through a proxy server also. Reach out to your Virsec SE/CST contact to configure Virsec Threat Intelligence.
VSP-Host collects file metadata from the workloads it protects during:
- Initial host scan from reference host during/after a host profile creation
- During runtime when a new, un-allowlisted file is executed
In cases where the trustworthiness of the files cannot be determined locally on the servers through OS level check or existing published allowlist, the metadata of those files is sent to CMS. On CMS, these files get populated in the allowlist section for further action by the user. At this point, VSP CMS also connects with Virsec Threat Intelligence via a REST API call over TLS channel and sends the checksum (only) of these reported files to get a reputation outcome as the response. These requests often send queries in bulk for multiple checksums and cache them locally on CMS for efficiency. A typical high-level outcome that VSP CMS would leverage would be:
- Malicious – The file is considered malicious based on the multi-level analysis performed by Virsec Threat Intelligence classification algorithm
- Suspicious - The file is considered suspicious based on the multi-level analysis performed by Virsec Threat Intelligence classification algorithm. This file may be declared malicious at a later time based on its threat profile
- Known - The file is presumed to be benign. The sample does not have any AV detections from trustworthy sources, and it does not match any of the internal threat signatures. In addition, these files also have been found to be valid with trusted software vendors. Files marked as SAFE by reversing labs also have a trust factor. VSP trusts only the files with trust factor values 0,1 and 2. Files with trust factor 3 and above are not considered as known by VSP
- Unknown - The requested hash is not present in the system or the system does not have enough data to make the Malware Presence calculation
With this analysis available, the files presented in the allowlist window are marked as either:
- Threat - For Malicious & suspicious files
- Safe - For known files
- Unverified - For unknown files
This allows the user to make allowlisting decisions, manually or automatically (using auto allowlist settings in host profile configuration).
In case a publisher/package is explicitly not allowed in the publisher/package list, that configuration takes precedence over the reputation received by Threat Intelligence Service.
In case a publisher/package is explicitly not allowed in the publisher/package list, files belonging to these entries are marked as threats in the edit allowlist section. No additional threat check is performed on these files.
In addition, CMS also reports additional information about malicious files as shown below:
- Threat Score - Based on the threat level sent by the threat intelligence service
- The full outcome of Threat intelligence query that can be reviewed by a click on the Reputation status file corresponding to each file