Trust Sight Introduction
- 28 Oct 2024
- 1 Minute to read
- Print
- DarkLight
- PDF
Trust Sight Introduction
- Updated on 28 Oct 2024
- 1 Minute to read
- Print
- DarkLight
- PDF
Article summary
Did you find this summary helpful?
Thank you for your feedback!
About this Article
This article provides an introduction to TrustSight
TrustSight provides visibility into the topology, vulnerability compensation, system integrity and software information of the customer environment. These widgets can be viewed at macro and micro levels to get a clear understanding of the existing environment. With this information, required actions can be taken to compensate the discovered security gaps.
Workflow
Here is the workflow for TrustSight at a high level:
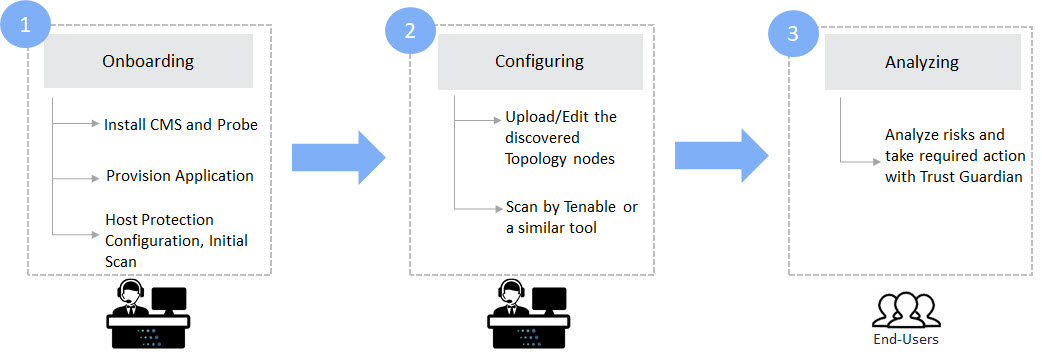
- TrustGuardian components (CMS and Probe) are installed. The Applications/Workloads are provisioned. Host Protection is enabled for an initial scan of all the executables on the Probe machine
- Configuration:
- After completion of Step 1 and 2, Trust Sight provides the statistics of the procured/discovered information
Features
To access TrustSight, navigate to TrustSight in the CMS left navigation pane. There are four basic widgets provided by TrustSight to understand the current pulse of the environment:
Was this article helpful?
