About this Article
This article provides an introduction to Virsec TrustHub and its types.
Virsec TrustHub is the repository that is utilized to determine the Trust Score of the executables discovered on workloads. The TrustHub components are a part of the Trust Blade Engines - Blades 1c and 1d - associated with Provenance.
Through TrustHub, Virsec aims to cover all the packages that may exist in the workloads:
- First-party code that is developed by the customer and any (third-party general or customized) code where customer has ownership through their vendors (Ensure that this code is provided to Virsec)
- Third-party code from the customer's vendors (ISV-provided code that exists on the workloads)
NOTE
- Virsec does not store any code in our TrustHub repository. Only metadata related to the packages are stored that allows to determine which files are trusted
- A third-party unpacker service is utilized to unpack packages with various file formats
Trust in Supply Chain

- ISV Repository – Virsec Global TrustHub is a common repository for third party code that is expanded continuously using nightly processes to provide maximum coverage for common OS files. If any third party package does not have a match in our Global TrustHub, it triggers an email to the Hub Admin with the package information. This package is then added to the global repository. Click here for more information
- Customer Repository - Enterprise TrustHub is a customer-specific repository for their code that can be expanded by providing the code repository information in CMS. Click here for more information
- Workload - Maintenance Mode is an intermediate mode for configured hosts. In this mode, the probe goes into an “observer” state, allowing the execution of new packages during the change control window. No Incidents are reported and new executables are automatically added to the allowlist
- Sandbox Analysis (Work in Progress) - Trust score for executables are determined based on the execution of the files in a Sandbox environment
- Auto-Allowlist - When this option is enabled, files with equal and above the configured Trust threshold value in Host Profile are auto allowlisted for the workload
TrustHub in Action
In this section we look at the TrustHub working through a workflow:
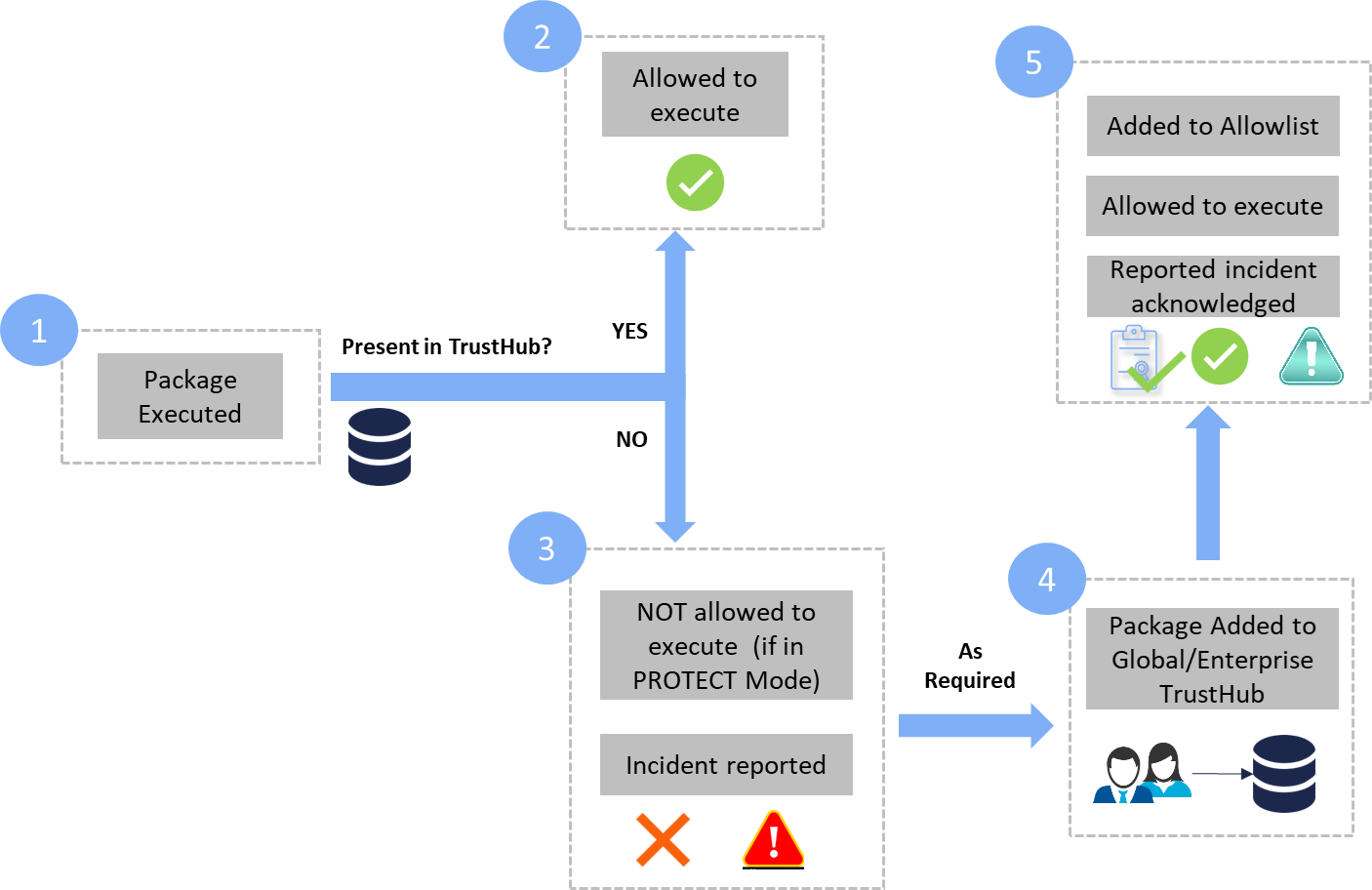
- Whenever a package is discovered on a workload or repository, based on Trust Score determined by the Trust Blades Engines, it is determined whether the package is allowlisted or not
- In cases where the TrustHub determines that the package is safe, the reason in the allowlist is displayed as "Trusted by TrustHub". This can be viewed in Host Profile > Edit Allowlist
- Hover the mouse over the Trust Score indicator to view
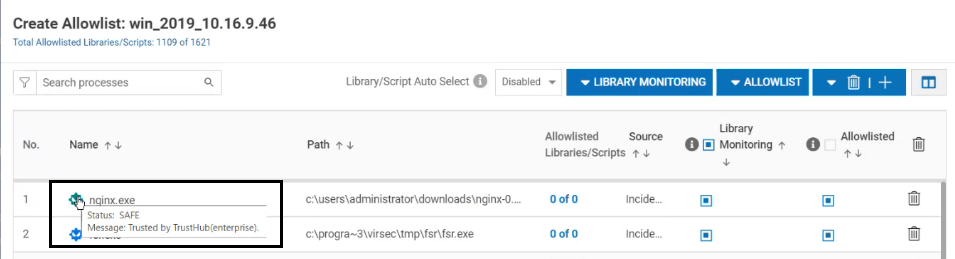
- Alternatively, click on the required allowlist entry
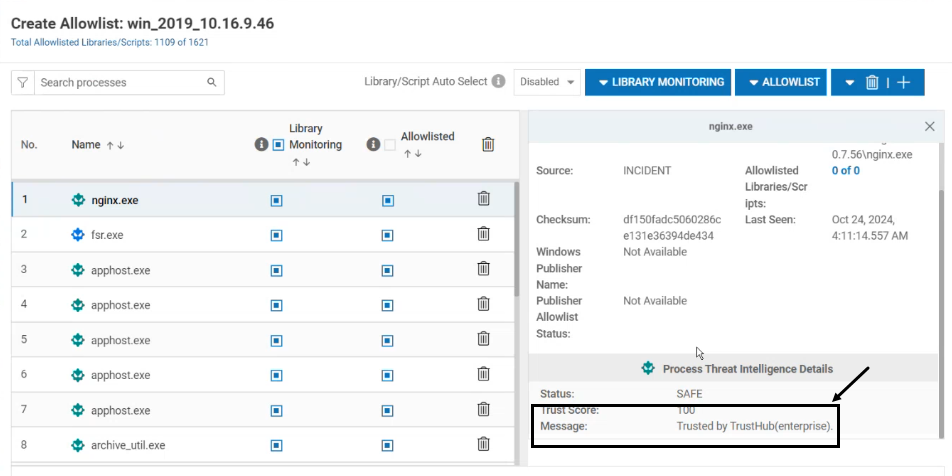
- Hover the mouse over the Trust Score indicator to view
- In a scenario where the file is not trusted, a validation is performed on the package. If the file is not found safe:
- It is not allowed to execute if PROTECT mode is enabled
- A corresponding incident is reported
- If the validation is successful, depending on the executable and requirement, it can be either added to Enterprise (through Trusted Repositories) OR Global (through Virsec team) TrustHub. The added entries are scanned and updated once in 24 hours through an automated process
- Before this 24-hour period, the package is NOT added to the allowlist and the status is shown as "Pending"
- Once the entries are updated,
- Package is added to the allowlist
- It is allowed to execute and no incidents are reported
- Existing incidents related to the package are auto-acknowledged